Penetration testing uses creative, blended attacks like real-world adversaries to find weaknesses in tested systems. By simulating real-world attack scenarios, pen testing is
invaluable for locating and assessing system configuration issues, hardware and software flaws, and deficiencies in countermeasures.
A penetration test is a great way to identify and assess vulnerabilities. However, you can only discover those weaknesses in the places you look –the test's scope or attack surface. When an organization determines the scope, they often define a smaller attack surface than the one the attackers can find. If you do not first perform a discovery operation of the actual attack surface, your pen test might leave critical vulnerabilities undiscovered.
Auditor Approach
In the context of pen testing, the auditor approach uses a checklist and tests things you already know you have. However, in today's rapidly changing zero-trust environments, there is a high probability that new vulnerabilities like shadow IT, converged or expanded networks, exposed passwords, or new vendor relationships have created new vulnerabilities.
This type of audit aims to check the boxes and submit a compliance report. But does it make the organization more secure?
Feedback loops are one common pitfall that can completely rob you of the ROI you otherwise receive with quality penetration testing. Without completing an Attack Surface Analysis (ASA) before pen testing, you leave an ever-expanding gap between the perceived attack surface and the actual attack surface. This is what we refer to as a feedback loop.
The actual attack surface is where real attackers will strike.
Feedback Loop Defined:
What is a feedback loop? A feedback loop is a cyclic process where testing repeatedly uses the same input and scope, getting the same results. However, the perceived attack surface and the actual attack surface may differ, leaving considerable gaps in vulnerability detection. You can't defend what you don't know about, and your adversaries don't follow the rules.
'"That's out of scope!" - Said no attacker. Ever.' Drew Porter
'Never underestimate the creativity of a desperate adversary.'
William Suthers, Director of Technical Services at Truvantis
If your organization is starting to experience a pattern of repeated behavior with a limited value from security testing efforts, you might be a victim of pen testing feedback loops. Your process could likely benefit from a new surface attack analysis and threat landscape gap assessment specific to your business environment.
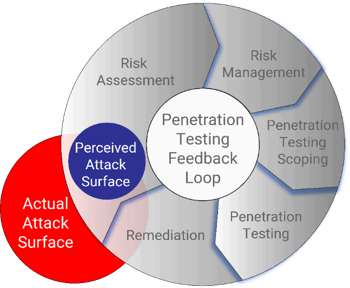
Things change, so shouldn't the testing scope change as well? The answer is yes. The penetration testing scope should continually evolve based upon an informed third-party discovery process. When we don't constantly update, we find ourselves trapped in a feedback loop, questioning why we've lost the value we once obtained from cybersecurity pen-testing operations.
Please read this blog for more on combating feedback loops.
Attacker Approach
Before defining your scope, it's best to conduct an objective ASA. Your organization is an ever-evolving machine driven and managed by a mix of humans and technology, which must evolve to remain competitive and stay ahead of the evolving threat landscape. As do real-world attackers, an attacker approach to penetration testing begins with an ASA. It is far better to have your attack surface discovered by an ASA than by an actual attacker.
A quality Attack Surface Analysis replicates the techniques of a real-world attacker in searching for unexpected ingress vectors. It begins with what you think your attack surface is, and then testers solicit information about your organization using OSINT (Open-Source Intelligence) sources just as real attackers do. The tester will take your domain and other information and crawl through the attack surface, deep and dark web to look for:
- Exposed Internal Data
- Indicators of Malicious Activity Including "Chatter," - what's being discussed about you, what's being bought and sold
- Breach Data Associated with Your Organization
- Related or Spoofed Domains
It would help if you also looked at your surface internet footprint for indicators of compromise or other potential attack vectors. Then, review and make necessary changes to the scope to include previously unconsidered ingress vectors.
Attack Surface Analysis Steps
Without an Attack Surface Analysis, you will fail to find all your risks. It would help if you looked at your organization like your adversaries. If you do not update your understanding of your attack surface, the scope used for your last penetration test will be input for your current test cycle. The gap between the actual attack surface and your perceived attack surface grows with each cycle. This gap is where real-world attackers will strike.
- Perceived Attack Surface
Start with your perceived attack surface. Usually, this is the scope of what you would have expected to test before the analysis. - Open-Source Intelligence Reconnaissance
Crawl through the surface, deep and dark web to identify attack surfaces that you did not know you had. Please read this blog for more on Using OSINT for ASA. - Data Reconciliation
Review the difference between your perceived attack surface and the discovered attack surface to confirm your ownership of those assets and services. - The Resulting Attack Surface and Revised Scope
The resulting understanding of your attack surface can now be used to update the scope for your penetration test. At this point, you have defeated the problem of feedback loops.
About Truvantis
Truvantis is a cybersecurity and privacy consulting organization with comprehensive expertise in implementing, testing, auditing, and operating information security programs. We specialize in helping our clients improve their cybersecurity and privacy posture through practical, effective, and actionable programs—balancing security, technology, business impact, and organizational risk tolerance.
Our Attack Surface Analysis replicates the techniques of a real-world attacker in searching for unexpected ingress vectors. First, let us know what you think your attack surface is, then we will solicit information about your organization using OSINT (Open-Source Intelligence) sources just as an attacker would.


.png)





.png)
