When it comes to security risk assessments, it often seems unclear what value you’ll receive in the report. Some assessors use meaningless overused buzzwords, and there are a lot of vague, confusing and misused definitions out there.
The problem is: you likely need a risk assessment for compliance. PCI DSS, SOC2, ISO 27001, NIST, HIPAA and other standards all consider a risk assessment an imperative part of a strong security program — and they’re right to make these important analyses a requirement.
A proper risk assessment is a fundamental building block for any company’s information security posture and we’re here to help you get the most value out of your assessment. But first, let’s start with the basics:
Important terms
Before diving into the fundamentals of conducting a risk assessment, it helps to first be familiar with some common language used in risk management:
Asset
An asset is a useful or valuable thing that carries a degree of risk, especially ones that have a significant degree of price volatility. These are the people, property or information we look to protect in risk management.
Both tangible and intangible items can be assets. Employees, customers, contactors, your reputation, proprietary information, databases, records, etc. can all be considered assets.
An example: Your website, for instance, is a huge asset to your business. Should it be hacked or compromised, it could mean huge problems for your company.
Threat
A threat is the thing or incident causing a risk, or anything that can exploit a vulnerability and affect an asset.
An example: A threat could be a phishing email. Upon clicking an infected file, your computer is exposed to malware.
Risk
Business Dictionary defines risk as “a probability or threat of damage, injury, liability, loss, or any other negative occurrence that is caused by external or internal vulnerabilities, and that may be avoided through preemptive action.”
While technically correct, the best way to define cybersecurity risk is the probability and magnitude of something bad happening at a future time. Usually it includes the possibility of losing some or all of an investment.
An example: Any asset and threat paired together can form a risk. For instance, a software program without proper user restrictions (the asset), may be subject to privilege abuse or data mishandling by an unauthorized employee (the threat) who exposes personal patient data (the risk).
What exactly is a risk assessment?
If you Google search the phrase “what is a risk assessment?,” Google’s answer box will serve you a dictionary definition.
It’ll say that a risk assessment is “a systematic process of evaluating the potential risks that may be involved in a projected activity or undertaking.”
While this definition is accurate, this formal and technical language can be unhelpful. In simplest terms, a risk assessment is a way to calculate the threats that could happen to your business.
It outlines the probability of these potential risks occurring so that you can make informed decisions about mitigating their likelihood of happening in the future. The risk assessment empowers smarter judgment calls by outlining each potential threat against a vulnerability and calculating the probability of the risk occurring.
Why is performing a risk assessment important?
There are a lot of myths about risk assessments, many used as justification not to get one. Some people assume that these analyses are too time-consuming, that they’ll tell you things you already know, or that they’re a waste of time if you already have “good security.”
In fact, all of the assumptions we discussed in the linked article above are untrue— and risk assessments are critically important!
Why? Here are three big reasons to invest in a risk assessment.
- Risk assessments help to protect you against breaches. Perhaps one of the biggest reasons companies choose to assess their risk is to protect them against costly and disruptive breaches. Risk treatments* can be ways to protect your business from cyberattacks and to better improve protection of private data.
- Risk assessments give you data to prioritize improvements to your security. It’s difficult (sometimes impossible) to make dozens of changes to your cybersecurity at once for technical, operational and budget reasons. A risk assessment makes it so you don’t have to. The assessment will help you to justify which areas need better protection, prioritize which critical matters need attention first, as well as help you to determine which risks you’re willing to live with.
- Risk assessments help to guide your security investment. It may be hard to see the value in investing thousands of dollars into improving its cybersecurity program. A detailed risk analysis will map out exactly which vulnerabilities take priority and why— outlining the impact each may have on your business if neglected. Once your stakeholders and investors see how much not making the changes could cost them, they may cast a more favorable eye on allocating the budget to risk treatments.
Risk Treatment Plan: Your treatment plan/table corresponds one-to-one with your risk scenarios, or the vulnerabilities paired with their potential threats. This plan details recommendations to reduce the likelihood of each risk occurring.
Types of security risks
When discussing the risks that can threaten your business, the list is long. However, most fall into a few “buckets.” We’ve detailed some of the most common types of security risks a risk assessment will address by category:
Financial
This is a threat that could cost your business a lot of money should it occur. It’s a dangerous possibility for your shareholders, investors or other financial stakeholders. Your leading motivator for having it addressed is to prevent capital loss.
An example: Investing a large sum of money in a new product line when you have a large debt that needs to be paid is a great example of a financial risk.
Operational
The impact of this type of security risk could halt the day-to-day operations of your business. It focuses on the internal processes you have in place, your employees and your systems.
An example: By ensuring all users on your systems are trained and authorized you can avoid mishandling of critical data.
Compliance
PCI DSS, SOC2, ISO 27001, NIST, HIPAA and other policies all consider a risk assessment an imperative part of any good security initiative. To violate or disregard their compliance terms can cost your business money in penalties.
An example: A vulnerability in the security of the software that houses your patient care records can violate HIPAA compliance protocol if compromised and is a prime example of this type of threat.
Legal
If a vendor loses PII/PHI that you entrusted to them, that's a violation of HIPAA, GDPR, CCPA etc. Not only will you pay a compliance penalty, but these are laws— and breaking them can land you in court.
An example: Patient information could be leaked in a number of ways, like through a hack or theft, and instantly become a legal matter.
Information security
Even if your business doesn’t have the same strict compliance protocols as health care providers, many companies do have customer data that requires safeguarding. An information security risk poses a threat to any sensitive or private data you house.
An example: Having outdated virus software can leave individual employee devices at risk of a ransomware attack. A bad agent could gain access to personal addresses, emails, phone numbers, etc.
Reputational
Reputational risks threaten your brand or company, breaking trust with those you conduct business with. This effect on your public perception can mean major loss of revenue and can be triggered directly by the actions of your employees, your partners, or suppliers.
An example: A reputational risk might be having a weak password on your company’s social media page, whereas it could be hacked and a bad agent poise as your brand’s voice online.
Security frameworks
When you run a risk assessment, there are certain structures you can follow, or foundations for performing the assessment. Here are some of the most popular security frameworks and standards for processes:
ISO 27005
This is known as the international or British standard for performing risk assessments. Technically speaking, those complying with ISO 27005 are complying with ISO 27001 and 2, as a subcomponent.
ISO is the mostly widely accepted framework for risk assessments and it follows a commonly known process. First, the scope* of the assessment is defined, as well as a list of assets within that scope. Then a vulnerability analysis is performed. During this process, a threat catalog* is used to match each potential threat actor with a vulnerability and asset— which is compiled into a risk scenario. Lastly, a treatment plan/table is made, which corresponds one-to-one with each risk scenario. This details recommendations to reduce the likelihood of that risk.
The recommendations in an ISO framework include more generalized solutions than the alternate NIST framework. This often allows for more creative problem-solving internally for mitigating risk. Commonly, many assessors perform a hybrid risk assessment, combining the frameworks of both ISO and NIST, which we’ll elaborate on below.
Scope: Your scope defines your boundaries, or how you’re choosing to limit your assessment / your risk management plan. It should detail the purpose of the assessment and which assets are being analyzed.
Threat Catalog: This is a list of generic threats that are often seen in risk assessments. They include events, actions, inactions and more that could mean bad things for your information security assets and are used to match each potential threat actor with a vulnerability and asset.
Threat Vectors: Each treatment plan will also consider threat vectors. These are the different routes that bad actors or attacks may take threaten your business security. For instance, your network might be a vector, or your email, which hackers can use to steal information.
NIST 800-30
NIST 800-30 is the United States standard framework for risk assessments, detailed by the federal government. It utilizes the same core building blocks as ISO above, following a similar structure for performing assessments.
What differs between NIST and ISO is the treatment plan, which is radically more specific in the NIST framework. NIST is more heavily prescribed, following a more concise algorithm for solutions. You’ll receive very specific recommendations for mitigation, much like following the exact measurements (akin to adding one tablespoon of sugar in a recipe versus a vague measurement or solution like a “dash of” this or that).
To some, this extra precision is helpful — giving them clear instructions. For others, it’s viewed as “bloat,” limiting their ability to problem-solved on a personal case basis.
FAIR
Factor Analysis of Information Risk (FAIR) focuses solely on quantitative assessments, not qualitative. These probability distributions put a heavy emphasis on numbers and metrics, which requires the expertise of statisticians, savvy cybersecurity personnel and massive amounts of data to crunch.
The FAIR framework can work well for mature cybersecurity programs, but if your company hasn’t been tracking its KPIs or doesn’t have lagging indicators, you will be forced to start with a more qualitative approach.
OCTAVE
OCTAVE stands for Operationally Critical Threat, Asset and Vulnerability Evaluation. It’s performed in two forms, S and Allegro, where small businesses follow more simplified steps while large enterprises follow another more comprehensive version. Typically it begins with building asset-based threat profiles, identifying infrastructure vulnerabilities and developing a plan.
This security framework is a great reference point for understanding how risk assessments are performed, but only commonly used for that: a reference.
ISACA RISK-IT
The ISACA RISK-IT framework is another example of a means to learn or teach how to perform a risk assessment rather than being used as a standalone process in-and-of-itself.
It’s more of an academic tool, for risk practitioners to use as an example of a risk assessment format, and is much like a hybrid combination of ISO 27005 and NIST 800-30 principles.
Methodologies for evaluating risk
In order to obtain estimates of your risk, you must operate by an assessment methodology. There are two main methods for analysing your risk: the quantitative and qualitative approaches, as well as hybrid methodologies that consider bits and pieces of both.
Quantitative risk assessments
In order to “quantify” the impact of the risk in terms of dollars and time (or contingency reserve), you’d then run a quantitative analysis. This helps to project the expected monetary value of addressing your risk and gives you another level of prioritization for managing it.
A proper quantitative risk assessment will demonstrate the return on investment that the company will get on its IT security investments to better justify the value of performing one with your C-suite.
But what is a quantitative risk assessment, really?
Risk is quantified or measured in terms of definite numbers, figures, and percentages, and/or probabilities. This methodology answers the question (among others) of, “What is the financial impact of risk?” and, “How much data would be lost or compromised if a risk were realized?”
This approach takes into consideration the “real” impact that a risk could have on business and operations looking at risk through a numbers-based lens.
How do you perform a quantitative risk assessment?
To get started with a quantitative risk analysis, an assessment team must first identify key assets to the business. This would include IT equipment, data processing systems, and facilities, along with less-obvious assets like employees, mobile devices, and the data itself which resides on the system.
Once all key assets are identified, you then calculate the value of each in dollars. This may be difficult to do for ambiguous or volatile assets, but it doesn’t have to be a perfect science; estimates are fine.
For each risk, determine which asset(s) it would affect and how much of that asset would be lost or compromised as a percentage. Then, simply take this equation:
An example: the loss percentage X the value of the asset = dollar amount of loss for that risk.
What you’ll get from a quantitative risk assessment
Quantitative risk assessments deal with estimating loss based on a financial perspective by using calculations like Single Loss Expectancy (SLE) Annualized Rate of Occurrence (ARO) and Annualized Loss Expectancy (ALE) Additional terms include: Exposure Factor (EF) Frequency (F) Control Strength (CS).
When taking a quantitative approach to risk, the assessment team will end up with a calculated value and potential cost for each risk in the risk register*, as well as the projected ROI for each advised recommendation in the risk treatment program.
By assessing each risk scenario in this way, the team should have a report of which assets are exposed to risk, and what the financial impact would be if the risk were realized. This allows management to make informed decisions when considering additional controls and safeguards to protect various assets:
If the control costs more than the amount that would be lost in a risk scenario, it doesn’t make financial sense to implement the control, regardless of whether the loss actually happens.
Risk Register: Your risk register ranks all your potential threats by priority with a “risk score.” This provides clarity around which risks are most important to address, and to track your success year-after-year in addressing your vulnerabilities and threat landscape.
Considerations before performing a quantitative risk assessment
The downside to this numbers-based approach is that it requires good data to use as input values which can only come from a fairly mature security risk program which has good historical data in the form of KPIs and KRIs.
Additionally, a fully quantitative risk assessment may be a hard sell to many organizations, as they tend to be less common and therefore less familiar. Quantitative risk assessments tend to be perceived as resource intensive and costly endeavor.
Qualitative risk assessments
This assessment looks at the “quality” of the risks, using the equation:
Risk score = probability of the risk occurring x impact of it happening
This risk score helps to prioritize your risks, so you know which are most important to address based on how they rank in your scoring system.
But what is a qualitative risk assessment, really?
The other risk assessment approach is to take a qualitative view on risk. Rather than working with hard numbers, metrics and values that you derived from data and from lagging KPIs and KRIs, you rely on the years of experience of the Information Security Professional and their expert opinion.
The qualitative approach is much more subjective than its quantitative counterpart in that it seeks the opinions and viewpoints of various business stakeholders when performing an assessment.
How do you perform a qualitative risk assessment?
A qualitative security risk assessment can be faster to achieve than its quantitative counterpart. However, this does not make the analysis less useful.
This method can involve subject matter experts (SME) from various parts of the business to discuss how their teams would be affected by different risks. For example, when assessing the risk posed to a server cluster, the assessor can ask, “How would your team’s productivity be affected if they couldn’t access their web application?”
Without a backup procedure in place, the answer would probably be that the team couldn’t produce anything, thus allowing the assessor to determine that the system is subjectively critical to business function.
For the most part the qualitative assessment relies on the knowledge and experience of the assessor conducting the assessment and his or her sagely advice. Still, this expert opinion can be very valuable to companies making decisions about risk-based information security budgeting and spending.
What you’ll receive from a qualitative risk assessment
The deliverable from a qualitative assessment should be a report of which assets and systems are most important to various parts of the business.
The assessment won’t necessarily show the financial impact if these systems were compromised, but will articulate which business units would be affected and how much productivity would be lost in different risk scenarios.
Additionally, the assessment will show the potential impact to the company’s reputation and any PR considerations if a risk were realized and became publicly known.
Hybrid risk assessments
When developing the security risk assessment methodology for your organization, it’s important to realize that both quantitative and qualitative analyses are valuable for a well-rounded risk view and risk management process. That’s why many of the most well-rounded assessors perform a mix of both types of assessments to provide the widest breadth of recommendations.
Risk appetite vs. risk tolerance vs. risk capacity
Implementing organization risk management means determining the risks that your company will accept, transfer, mitigate, or avoid. Successes in business requires taking some level of risk, but just how much?
Risk management requires not only understanding of impact, but also creating a risk management plan and understanding framework which sets the acceptable levels of risk to enable effective business operations. In order to set these levels, it is very important to know and understand and articulate your company’s risk appetite, your risk tolerance, and your risk capacity.
Let’s look at the differences below:
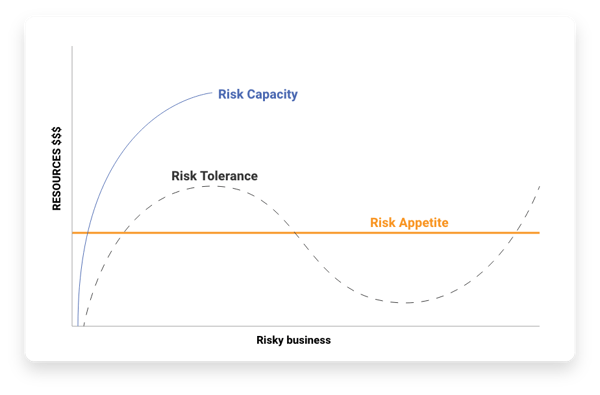
Risk appetite
This is the amount of risk you are comfortable with taking.
The casino analogy: If you were at a casino betting on a game, this is how much money you would be okay losing. You may have even expected this loss. It’s your company’s acceptable amount to lose should a risk become an issue.
Risk tolerance
This is the maximum amount of risk you are generally willing to take.
The casino analogy: This would be the maximum bet you’d lay on the table without a severely damaging loss. It would hurt to lose and may set you back for a bit, but you could realistically recover.
Outlining a clear risk profile* will detail a company’s willingness and ability to take on or avert each risk.
Risk Profile: As we explained above, a risk profile evaluates your company’s willingness and ability to take or avert a risk. Your company's assets and liabilities are often reviewed to see if you would be able to financially withstand the consequences of this risk should it occur (the ability), as well as your comfortability with it (the willingness).
Risk capacity
This is the amount of risk which if realized becomes completely untenable or disastrous for the organization.
The casino analogy: This is a loss so large, you’re walking away in the negative. Should these risks occur, you cannot recover from the cost: AKA, you’re out of business. You should never even come close to not addressing risks that could put you at your capacity.
Controls in risk assessments
In order to protect your assets, risk assessors will look at ways of increasing your control strength*, or your level of protection, with various forms of “control.”
Let’s look at three types of risk assessment controls with real examples:
Administrative controls
Think of this as managerial restrictions, aimed at reducing risks. These are often policies or other governance controls put in place to reduce your threat landscape.
An example: A policy to not post any business-related information online is a prime example of administrative control, protecting your intellectual property and company secrets. Repercussions for breaking the policy can match the extreme of the impact, ranging from suspension or firing to legal action.
Technical controls
These are often virtual barriers for safeguarding assets. This typically covers something you have (like physical keys), something you know (like a 6-string digital lock code) or something you are (like your fingerprint on a scanner to unlock a room).
An example: While we mentioned a few instances above, the most commonly thought of technical controls are probably firewalls, encryption methods and multi-factor authentication (MFA)— all creating a virtual barrier between a threat and your asset.
Physical controls
These are tangible walls or structures that can reduce the likelihood of a threat physical reaching your asset.
An example: Implementing badge access requirements to enter a room is an example of adding physical control over your assets, as well as mounting security cameras or positioning human guards around the site of your asset.
Control Strength: Certain controls need stronger protection than others based on the impact the risk would have to an organization should it occur. For instance, you may have a room that needs a bank vault-strength barrier versus an average door to protect an asset from theft. Installing this physically stronger door offers a higher control strength. In another instance, switching from password-only access to multi-factor authentication will grant you higher control as well.
Security qualifications
Just like any trade, those conducting risk assessments require expert training. In this section, we’re going to review the most important security qualifications or certifications that any qualified risk assessor should have to offer a deep breadth and depth of knowledge in the field.
CISSP
The Certified Information Systems Security Professional (CISSP) qualification is considered a baseline certifications for any reputable, experienced risk assessor. It’s equivalent to a right of passage in this field, as the defacto certification for information cyber security.
CISSP covers eight domains:
- Domain 1. Security and Risk Management
- Domain 2. Asset Security
- Domain 3. Security Architecture and Engineering
- Domain 4. Communication and Network Security
- Domain 5. Identity and Access Management (IAM)
- Domain 6. Security Assessment and Testing
- Domain 7. Security Operations
- Domain 8. Software Development Security
“Candidates must have a minimum of five years cumulative paid work experience in two or more of the eight domains of the CISSP CBK” to pass the certification.
CRISC
The Certified In Risk and Information Systems Control (CRISC) qualification is a risk-focused examination paired with work experience requirements in IT risk management. This is a more advanced specialization for those in the information cyber security realm to pursue.
CRISC covers four domains:
- Domain 1. IT Risk Identification (27% of exam)
- Domain 2. IT Risk Assessment (28% of exam)
- Domain 3. Risk Response and Mitigation (23% of exam)
- Domain 4. Risk and Control Monitoring and Reporting (22% of exam)
This certification is “awarded to IT professionals who identify and manage risks through the development, implementation and maintenance of information systems (IS) controls” and is a prestigious accomplishment for any risk assessor to earn.
When seeking a risk assessment team, be sure to inquire about their years of practice and to review their certifications. The right assessor will have a mix team of versed and skilled professionals with the portfolios to prove it.
Financial risk terminology
Risk management involves mathematical forecasting to project the potential damage of a risk occurring. There are a few terms that are important to know when calculating the possible impact of a risk
Exposure factor (EF)
This metric is a subjective estimate of the potential percentage of loss to an asset should a threat occur. For instance, if the value of the asset were to be reduced by two thirds, the exposure factor value is 0.66 or 66%. This percentage is then used in tandem with the asset value to calculate the next term: single loss expectancy.
Single loss expectancy (SLE)
This is the monetary value of a risk occurring on an asset. It’s defined by the following equation:
Single loss expectancy (SLE) = asset value (AV) x exposure factor (EF)
Annual rate of occurrence (ARO)
Next, you’ll need to determine the annual rate of occurrence. This is the probability and frequency of that risk occurring in a particular year, on average.
For instance, if you expect your office to be flooded once a decade, then the ARO is 0.1. So if the cost of a flood is $100K, then your ALE is $10K per year.
This metric is used to calculate annualized loss expectancy (ALE).
Annualized loss expectancy (ALE)
After determining the single loss expectancy and annual rate of occurrence, multiple these factors with the following equation to get your final result:
Annualized loss expectancy = Single loss expectancy (SLE) x annual rate of occurrence (ARO)
ALE is used to weigh the pros and cons of choosing a risk treatment option.
Risk treatment options
Addressing your risks can take many forms, such as to accept, transfer, mitigate, or avoid the potential situation at hand.
Let’s explore the four ways to treat a risk:
Acceptance
To accept a risk might mean that after weighing your options for reducing it, it makes the most sense to make no changes, or to take the chance of it occurring.
Why you might accept a risk: Perhaps this particular risk matches your risk appetite, meaning the potential loss is something you can live with as sacrifice for focusing on other more important or time-sensitive matters.
Transference
To transfer a risk might mean that after weighing your options, it’s not your company’s problem to solve, but rather something you can pass on to its rightful owner.
Why you might transfer a risk: A company may choose to transfer risk to a third-party vendor. For instance, as a small retailer grows, they may choose to use Amazon services to sell goods online. Thus, they transfer the PCI DSS risk to that vendor.*
*While it might seem like the “easier” option to transfer a risk, consider the effects of the concept of residual risk. A hacker may breach a third-party, even Amazon. Thus, although the company tried to transfer the risk, a residual risk occurs. To protect against this residual risk, the online retailer needs to continuously monitor the vendor’s security stance.
Mitigation
To mitigate a risk might mean taking actionable steps to reduce the probability of it occurring or the intensity of its impact should it occur.
Why you might mitigate a risk: If not actively reducing the likelihood or impact of a risk occurring would cost your business a huge amount of time and money, it’s worthwhile to take mitigation steps. Mitigation is the most commonly used method for addressing risk, and includes many recommendations. One instance of mitigation would be to reevaluate and put in place preventative measures for reducing error in processes, automation or user interfaces.
Avoidance
To avoid a risk might mean to purposely exclude it from your considerations.
Why you might avoid a risk: Sometimes a security control is not cost effective— thus, an organization will choose to avoid the risk completely. For example, a small retailer may choose to mitigate in-store purchase risks, but avoid online sales since the risk mitigation of PCI DSS compliance is not cost effective for a new business.
Analyzing the results of your risk assessment
Without assessing your risk, you are spending money blindfolded.
Risk assessments offer a wealth of personalized data to reduce your threat landscape and increase your cybersecurity.
But remember, a risk assessment will only help your business if you use the data to make smart decisions and take tangible action.
Here is some expert advice to help you get the most out of your risk assessment, straight from our team at Truvantis®. We also have a blog focused on how to actually use your report to utilize your results to your full potential.
The Next Step: Learning How to Get Real Value from Your Risk Assessment
Here at Truvantis, our team is comprised of senior-level risk assessors with 10+ years experience and a range of impressive qualifications.
Still, the most important part of a risk assessment is taking action on what it recommends.
That's why we created a free whitepaper about six steps you can take to get real value out of your security risk assessment.
Click the button to get your free copy.
.png) Are you considering a security program for your organization? We work with clients just like you to implement a modern and reliable security program. Read our security program guide to learn what goes into a security program, who needs to be involved, and more to ensure long-term success.Learn More
Are you considering a security program for your organization? We work with clients just like you to implement a modern and reliable security program. Read our security program guide to learn what goes into a security program, who needs to be involved, and more to ensure long-term success.Learn More



