Red Team vs. Penetration Test vs. Vulnerability Assessment - Seven characteristics that set these services apart and why it matters to you.
Industry Driven Confusion
With an ever-changing threat landscape, security is a serious problem. Companies face the reality of imminent threats aimed at destroying their business. Vendors barrage executive managers and security professionals with industry-driven conflated messaging about various security assessment services.
Work in this industry for a few decades and it's incredible what you'll come across. I've seen vulnerability assessments labeled as both penetration testing and red teaming. Spend five minutes looking for security testing services and you'll quickly spot this. We call these sca{n|m}s.
Red teaming is often conflated with penetration testing. Oh yeah. This happens a lot. For instance, some vendors claim that a red team is simply an advanced penetration test that includes physical or technical attacks while remaining undetected. This position completely misses the point resulting in confusion and unmet expectations. Worse, incomplete testing strategies can leave unmanaged attack surfaces for attackers to use against you.
Red Teaming, Penetration Testing, and Vulnerability Assessments
Vulnerability Assessment
Intent - Review a target environment security against well-known security issues associated with opportunistic attacks: examples, malware signatures, unpatched software, open ports, and vulnerable services.
What they don't do - Vulnerability assessments expressly forbid exploitation and adhere to a narrow assessment scope. They don't provide validation or demonstrative impact. They are but just one component of a comprehensive defense-in-depth strategy.
Return on Investment - Provides reasonable assurances of residual risk associated with well-known security issues at a reasonable cost.
Penetration Testing
Penetration testing and red teaming are designed to inform the risk assessment through exploitation. Pen tests involve targeting, interacting, and exploiting preventative security controls. They identify risks associated with attacks well beyond opportunistic attackers and where possible, validate such facts through exploitation.
Though vulnerability assessments and penetration tests are very different, there is one very clear distinguishing feature – human cunning. Though automated tests such as vulnerability assessments have great value, without the involvement of a skilled adversary collecting data, establishing situational awareness, and then synthesizing potential exploits, they can not be considered a penetration test
Intent - Penetration testing measures the effectiveness of preventative security controls through exploitation. Pen Tests breach the target environment by circumventing preventative security controls and leveraging the environment against itself.
What they don't do – Pen Testing is conducted without regard to security response mechanisms or detection rates.
Return on Investment – Discovery, and validation of confirmed vulnerabilities by exploiting layered security controls and blended exploits. Pen test data allows the resource owner to make well-informed risk-based decisions about preventative security controls. The result is an overall reduction of risk that a determined attacker might have otherwise leveraged.
Red Teaming
While penetration testing measures the effectiveness of preventative security controls, Red Teaming measures the effectiveness of security response mechanisms. Security response mechanisms associated with defense-in-depth strategies consist of a collection of detective, preventive, and corrective security controls related to one or more of the three pillars of security (technical, administrative, physical). To achieve this, unlike vulnerability scans, pen testing, and cyber-criminals, Red Teams operate with the intent to get caught by the Blue Team eventually.
Often starting with surreptitious or covert methods of entry (S/CMOE) initially operating below detective security controls, Red Teams will continue to interact with security response mechanisms and escalate activities until they are detected and effectively managed. Getting caught, measuring the effectiveness of security response mechanisms and Blue Team interactions are distinguishing characteristics of Red Teaming.
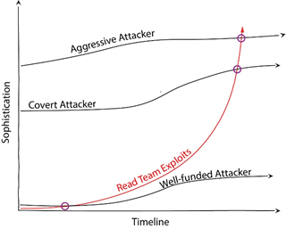
Red Teams simulate real-world attacks to measure detection thresholds and security response mechanisms.
Intent - Red Teaming measures the effectiveness of security response mechanisms. This requires a more resource-intensive approach to measure both detection and response of specific threats.
Effective Red Teaming requires active communication and coordination with key members of the Blue Team. Beyond just proving they can break in, the true goal of Red Teaming is to assist Blue Teams in fine-tuning the detection thresholds and security response mechanisms of defense in depth strategies until the desired performance metrics are satisfied.
Examples of Security Response Mechanisms Targeted Through Red Teaming:
- Visitor Access Policy Management (Administrative, Physical) – Deter/ Detect
- Insider Threat Program (Technical, Administrative, Physical) – Detect/ Delay
- Rogue Device Management (Technical, Physical) – Detect/ Delay/ Deny
Return on Investment - Measurement of the effectiveness of security response mechanisms. Red Team activities help executives make well-informed decisions about the organization's overall security program. Businesses realize a significant risk reduction that opportunistic, determined, and well-funded attackers could have otherwise used against you.
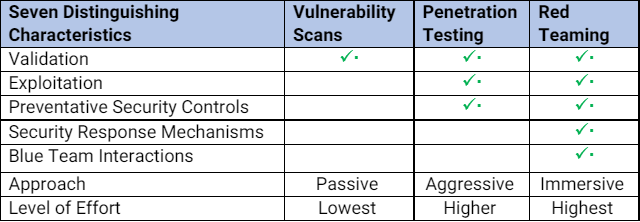
Seven Differentiating Characteristics of Security Testing
When asked about what's the difference between vulnerability assessments, penetration testing, red teaming, the following characteristics come to mind:
Which Approach is Best?
That depends on your business needs and security testing objectives. Comprehensive cybersecurity programs use them all, combined with attack surface analysis and forensics. On the other hand, companies often only need a specific test to satisfy immediate security requirements. Truvantis can help you customize the testing scope and details according to your strategic and tactical business plans.
The Truvantis Approach
We don't just sell things to customers; instead, we partner with our clients to ensure their success. Our service portfolio is flexible to meet and exceed your needs. We take an intelligence-driven approach to offensive security testing, from attack surface analysis to full-spectrum red team engagements, helping you avoid common security testing pitfalls.
Components of our comprehensive security testing include, but are not limited to:
Attack Surface Analysis
Helping our clients find a validated starting point for security helps combat security assessment feedback loops.
Vulnerability Assessments
We provide clients with a rapid non-evasive prioritized review of target environments.
Penetration Testing
Validates effectiveness of preventative security controls and provides perspective through the eyes of a real-world attacker.
Red Team Testing
Measures the effectiveness of security response mechanisms and ensures risk mitigation balances with the organizations' risk appetite.
Forensic Review
We help ensure clients have the forensic support they need when something goes wrong.
Contact Truvantis today to discuss your cybersecurity testing needs.


.png)






.png)
