Given the complexity and cost of security, privacy and compliance efforts, a comprehensive risk management program is the best overall approach. A combined program helps reduce duplicate efforts and optimizes the ability to adapt to changes. Privacy, cybersecurity and compliance may have distinct goals but are interdependent and in best-case scenarios, work together to build trust and confidence in your data management system.
The three essential elements of a comprehensive risk management program include: (1) Alignment of stakeholders; (2) Combed security and privacy risk assessment; and (3) Repeatable process.
Alignment of Stakeholders
The alignment of stakeholders when building a privacy program is the second essential element. The key stakeholders requiring alignment are Legal, Security, and Privacy. An adaptable risk-based privacy program depends on understanding the company's legal obligations and appropriately analyzing security risks.
Combined Security & Privacy Risk Assessment
Privacy regulations boil down to protecting information. In other words, privacy is about the security of data. The various privacy rights can be traced back to core security principles defined by NIST as Confidentiality, Integrity, and Availability (CIA). The different privacy regulations, regardless of approach, reach the same end: to protect the CIA of sensitive information. When organizations establish a firm foundation in security, they can implement controls along with security that can anticipate future regulations and evolve accordingly. The starting point is a proper risk assessment.
|
|
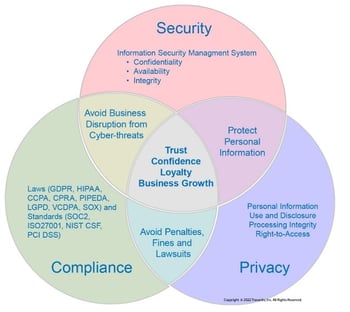
An effective privacy practice requires communication and coordination between security, privacy and compliance programs.
The last thing you want is for each discipline to operate in their bubbles. Failure to communicate and coordinate would result in wasted and duplicate work and leave gaps in one or more areas.
A holistic risk management program is the most effective way to manage Security, Privacy and Compliance.
A comprehensive risk assessment evaluates your cyber-threat landscape, applicable privacy rules and the complex compliance landscape. |
Repeatable Process
Another best security practice is using a repeatable process. Cybersecurity best practice has long relied on repeatable processes based on standards frameworks. A framework-based approach establishes consistency and reliability and can be adjusted as the threat landscape evolves and the organization matures.
The Truvantis Privacy Risk Program
If you are wondering where you stand regarding the CPPA and what you need to comply with the new law, consulting a Truvantis expert is an excellent place to start.
The landscape of privacy regulations is vast and continuously evolving. Truvantis can help you select and track which requirements are applicable. In addition, we can help build a solid central privacy program capable of supporting the entire matrix of international, federal, and rapidly changing state laws and regulations.
Ready to move forward? Contact Truvantis for more information and to schedule a privacy workshop.
Truvantis is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations and products. We specialize in helping our clients improve their cybersecurity posture by implementing testing, auditing and operating information security programs – balancing budget with risk appetite.


.png)





.png)
