Cybersecurity and privacy risks remain among the top threats facing business organizations today. Increasingly, boards are leaning on the CISO role to guide investments in cybersecurity and privacy programs, emphasizing the importance of risk management. This article highlights essential elements for getting the best value from a risk assessment. A risk assessment is the first step to building a comprehensive security & privacy risk management program.
Get Top-Level Buy-In
Endorsements and support from the Board of Directors and the C-suite are critical to the ultimate success of the risk assessment and your security & privacy program. Without executive support, the program will not be as successful as possible.
|
|
The Gartner Board of Directors Survey 2022 found that:
|
Identify the Purpose & Scope of Your Risk Assessment
Risk assessments are as extensive as you choose or need them to be. With this in mind, you must define what parts or aspects of your business will be assessed. For example, do you want to look at your entire enterprise or a specific application? Would you prefer to evaluate a whole department, a business unit or a single vendor or solution? The answers will inform the results and help define schedule and resource requirements.
Perform an Attack Surface Analysis (ASA)
Part of the risk assessment is determining your attack surface. The attack surface is the set of all possible points or vectors where an attacker can try to enter, cause an adverse effect, or extract data from your organization. Your existing and historical records help define your perceived attack surface or the one you knew about before beginning the new risk assessment. Because your attack surface changes continually, an ASA is essential to the current risk assessment.
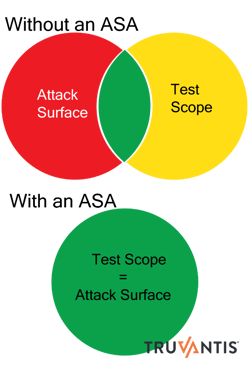
The attack surface you analyzed last year is out-of-date.
“That’s out of scope!” - Said, No Attacker Ever
Communicate Results & Educate Your Team
It’s important to convey to all stakeholders why you’re performing a risk assessment. This is the time to build excitement by reminding everyone they’re helping the entire organization improve its security!
Use Compliance as a Competitive Weapon
If you can effectively demonstrate that you’ve made efforts to comply with privacy and security laws, you can lower your risk of legal or administrative action. This is when it can be advantageous to earn a certification like SOC 2, PCI DSS or ISO 27701.
Implement Your Results
Get the most value from your risk assessment by actually doing something with your results. The assessment should outline possible action steps to address your risks and rank them by degree of importance so you have no excuse for not dealing with them.
Knock out the most urgent, cost-effective solutions first and allocate future budget for longer-term projects. Failure to act can leave you more vulnerable than when you started.
Leverage vCISO Services – The Benefits of an In-house CISO and Security Staff Without the Overhead Expense
Given the rise in cyber risk, the role of CISO has become vital to continuing business operations. However, when an organization is without a full-time CISO, a vCISO can backfill the gap or be a permanent, safe, cost-effective solution. Truvantis offers world-class vCISO services customized to the scope and objectives of your organization.
A qualified vCISO team gives you the same expertise, services, and benefits as a seasoned, highly certified CISO, but at a fraction of the cost. Look for a vCISO team bringing the following attributes:
- Experience and industry leadership
- A risk-based methodology for running your combined security and privacy program
- Communication and people skills
- Strategic advisor and executor of security, privacy and compliance programs.
- Executive-level reporting in business terms
- Monitoring and maintenance of mitigating controls
- Precise budget planning and scheduled execution
About Truvantis
Truvantis is a cybersecurity, compliance and privacy consulting organization with comprehensive experience implementing, testing, auditing, and operating cybersecurity and information privacy programs. In addition to cybersecurity, compliance and privacy services, we offer a suite of cybersecurity training courses and certifications. We are also a PCI DSS, Qualified Security Assessor (QSA).
We specialize in helping our clients improve their cyber governance posture through practical, effective, and actionable programs—balancing security, technology, business impact, and organizational risk appetite.


.png)






.png)
