The Health Information Trust Alliance (HITRUST) Common Security Framework (CSF) is a widely recognized security framework that HITRUST developed in 2007 to provide a roadmap to compliance for programs like ISO/IEC 27001 and HIPAA. HITRUST CSF incorporates security, privacy and other regulatory requirements from existing frameworks and standards to demonstrate their security and compliance in a streamlined fashion.
The HITRUST CSF Risk-based, 2-year (r2) Validated Assessment is globally recognized for demonstrating an organization manages cyber-risk effectively. r2 takes a risk-based approach designed to help organizations address their most demanding security and data privacy challenges.
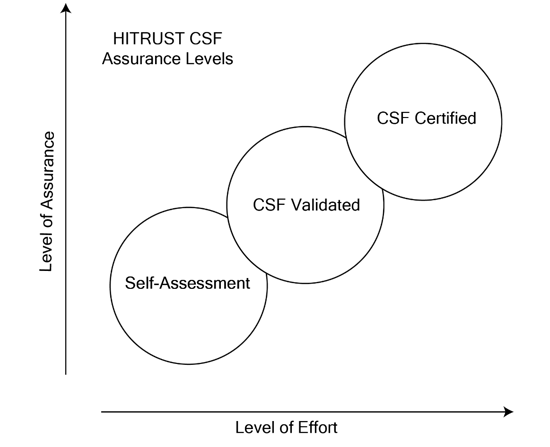
There are three degrees of assurance or levels of assessment in HITRUST: self-assessment, CSF-validated, and CSF-certified. Levels build on the one below it with increasing rigor. At the highest level, an organization meets the highest level of risk management assurance.
Is HITRUST Only for Healthcare?
HITRUST is governed by representatives from the healthcare industry, including Anthem, Kaiser Permanente and UnitedHealth Group. HITRUST created and maintains the CSF as a method for healthcare organizations and their providers to demonstrate their security and compliance in a consistent and streamlined manner.
Due to its rigorous, comprehensive, and effective approach, a HITRUST r2 Assessment and Certification is considered a gold standard in responsible risk management and compliance assurances. A proper r2 Assessment offers coverage against NIST SP 800-53, NIST CSF, ISO 27001, HIPAA, FedRAMP, FISMA, FTC Red Flags Rule Compliance, MARS-E Requirements, PCI DSS, CCPA, GDPR, AICPA Trust Services Criteria for Security, Confidentiality and Availability, plus more than 30 other industry-recognized frameworks, standards, and authoritative sources.
Experts expect that more organizations, especially in highly regulated markets, including financial services and retail, will choose to certify under the HITRUST CSF r2. For example, earlier this year, Microsoft announced that Azure and Office 365 are the first hyper-scale cloud services to receive certification for the HITRUST CSF r2. Similarly, in May 2022, global information management and digital services company Ricoh USA, Inc. announced it had achieved HITRUST CSF r2 certification.
i1 vs. r2 - Which Certification is Right for Your Organization?
The i1 certification is a one-year certification. It's a static set of 219 requirements that all organizations can undergo and get a certificate valid for one year.
The r2 used to be called the validated assessment. It stands for risk-based 2-year certification, and that two-year certification is a bit more involved.
The HITRUST CSF r2 Examines:
- Policy – Is there a policy in place?
- Process – Is there a process or procedure to support the policy?
- Implementation – Has it been implemented?
- Measure – Is the system being measured and tested?
- Managed – Are the measured results being managed?
Note: A separate NIST CSF Report is provided with the r2 Validated Assessment Report detailing an organization's compliance with NIST Cybersecurity Framework-related controls included in the HITRUST CSF framework but is not part of an i1.
The i1 is easier, whereas the risk-based r2 is more work but ensures a higher risk management maturity level. With r2, you could have 1,000 requirements based on your organization's risk factors. It comes down to what your customers will be willing to accept. If your risk as an organization is deemed low risk, there's a good chance they will accept the i1. But some organizations might view you as a higher risk and require you to complete an r2. When deciding which one your organization should be doing, the best thing to do is talk to your customers and understand their requirements.
About Truvantis
Truvantis is your HITRUST CSF business partner. Our experienced practitioners understand the challenges of securing data management systems and will work hard to understand your business objectives and develop a customized certification roadmap. Truvantis has a proven methodology for helping clients succeed in security compliance and certifications.
Truvantis is a cybersecurity, privacy and compliance consulting organization. We specialize in helping our clients by implementing, operating, auditing and testing information security programs that work – balancing budget with organizational risk appetite. Contact us today to speak with a cybersecurity, privacy and compliance expert.


.png)





.png)
