When it comes to cybersecurity, privacy & compliance, the road forward is often unclear.
The recently amended FTC Safeguards Rule (Title 16 Chapter 1 Subchapter C Part 314, 'Standards for Safeguarding Customer Information') went into effect December 9, 2022. The amended rule details what must be included in a "comprehensive security program."
What Businesses are Covered by the Safeguards Rule?
Any organization that is defined as a "financial institution" which may be broader than you think. "Financial institution means any institution significantly engaged in financial activities or activities incidental to such financial activities." – FTC
The Safeguards Rule applies to financial institutions subject to the FTC's jurisdiction that aren't subject to the enforcement authority of another regulator under section 505 of the Gramm-Leach-Bliley Act, 15 U.S.C. § 6805.
How do you know if your business is a financial institution subject to the Safeguards Rule? First, consider that the Rule defines "financial institution" in a way that's broader than how people may use that phrase in conversation. Furthermore, what matters are the types of activities your business undertakes, not how you or others categorize your company.
Examples of Financial Institutions under the FTC Safeguards Rule:
- A retailer that extends credit by issuing credit cards to consumers directly
- A car dealership that leases automobiles for 91 days or longer
- A real estate appraiser
- A career counselor specializing in individuals currently or formerly employed by a financial organization
- A business that prints and sells checks
- A check cashing business
- An accountant or other tax preparation service
- A travel agency that operates in connection with financial services
- An investment or credit consulting service
- An agency acting as a finder in bringing together one or more buyers and sellers
Information Security Requirements for Businesses Covered by the Safeguards Rule
In LabMD, Inc., versus Federal trade commission, March 2019, the 11th Circuit Court criticized the FTC for requiring comprehensive security programs but saying "precious little about how this is to be accomplished." Since then, the FTC has been evolving to get more detailed on what it means to have a "comprehensive" program in this and other FTC orders.
For example, on January 9, 2023, the FTC issued a complaint against Drizly, LLC, an online alcohol sales & delivery platform, for "failing to use appropriate information security practices to protect consumer's
personal information. These failures allowed a malicious actor to access Drizly's consumer database and steal information relating to 2.5 million consumers."
According to § 314.3 Standards for safeguarding customer information:
Develop, apply, and maintain a comprehensive information security program. The program must include administrative, technical, and physical safeguards customized to your organization's size and complexity, the scope of your activities, and the sensitivity of customer information.
Comprehensive Information Security Program - Objectives
- Insure the security and confidentiality of nonpublic personally identifiable financial information
- Protect against anticipated threats to the security or integrity of data
- Protect against unauthorized access to or use of such information
What are the Requirements for a Comprehensive Information Security Program?
Information Security Program Requirements - According to § 314.4 Elements:
Qualified Individual
Designate a qualified individual responsible for overseeing, implementing, and enforcing your information security program. The Qualified Individual may be an in-house employee, an affiliate, or a service provider. When using a service provider or an affiliate, you shall:
- Retain responsibility for compliance with this part;
- Designate a senior executive responsible for direction and oversight of the Qualified Individual
- Require the service provider to maintain a reasonable information security program.
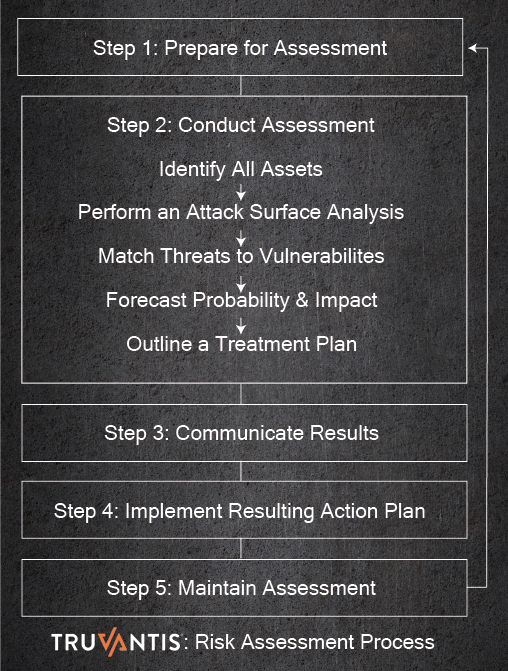
Risk Assessment
Base your security program on a risk assessment. A risk assessment identifies reasonably foreseeable internal and external information security, confidentiality, and integrity risks. Consider risks that could result in the unauthorized disclosure, misuse, alteration, destruction, or other compromises of such information. Assess the adequacy of any safeguards in place to control these risks.
Periodic Review of Access Controls
Implement and regularly review access controls, including technical and physical security controls, to:
- Authenticate and permit access only to authorized users
- Limit authorized access to only the information that users need to perform their duties and functions
Asset Inventory
Identify assets, including devices, systems, data, personnel and facilities used in your business relative to their importance to your objectives and risk strategy.
Encryption
Employ encryption to all sensitive information held or transmitted by you both in transit over external networks and at rest.
Secure Development Lifecycle
Adopt secure development lifecycle practices for in-house developed applications. Have procedures for evaluating, assessing, or testing the security of externally developed applications you utilize.
Multi-factor Authentication
Implement multi-factor authentication for all users accessing any information system.
According to the 2022 Verizon DBR, over 80% of breaches can be attributed to stolen credentials. There's been an almost 30% increase in stolen credentials since 2017, cementing it as one of the most tried-and-true methods to gain access to an organization for the past four years.
"We have continued to see poor password practices as one of the leading causes of data breaches dating back to 2009. It is particularly disconcerting that so many large breaches stem from the use of default and/or shared credentials, given the relative ease with which these attacks could be prevented." (2009 DBIR page 17)."
Secure Disposal of Data
Develop, implement, and maintain procedures for the secure disposal of customer information not later than two years after the last date the information was needed. In addition, periodically review your data retention policy to minimize unnecessary data retention.
Change Management
Changes in your environment can introduce new vulnerabilities. Adopt procedures for change management.
Continuous Monitoring
Implement policies, procedures, and tools to monitor and log system activity. Monitor authorized users and detect unauthorized access or use of, or tampering with, customer data. Periodically test or otherwise monitor the effectiveness of critical controls, systems, and procedures. Evaluate and tune your information security program in light of the testing and monitoring results.
Training
Provide your personnel with security awareness training. Update training material to reflect new risks identified by the risk assessment.
Manage Service Providers
Select service providers capable of maintaining appropriate security and integrity of customer information. Require your service providers by contract to implement and maintain such safeguards. Periodically assess your service providers based on the risks they expose and the continued adequacy of their security controls.
Incident Response Plan
Create a written incident response plan designed to promptly respond to and recover from any security event affecting the confidentiality, integrity, and availability of sensitive information in your control.
Regular Reporting to Leadership
Your Qualified Individual must report at least annually, to your board of directors, equivalent governing body or to the senior officer responsible for your information security program. The report shall include material matters related to the information security program, including:
- Risk Assessment
- Risk Management and Control Decisions
- Service Provider Arrangements
- Results of Testing
- Security Events or Violations and Management's Responses
- Changes recommended to the Information Security Program
"While the FTC is continuing to evolve in describing what constitutes a reasonable comprehensive security program in the Privacy context, an entire body of work already exists in the security space that describes in excruciating detail what makes a comprehensive security program. Covered 'Financial Institutions' should not just rely on what the FTC has included under the rule, but should also consider existing best practices for NIST, CIS, ISO, etc. "
– Jerrod Montoya JD, CIPP/US
If you build your security & privacy program on a well-established industry framework, new laws and regulations like the recent FTC updates need not significantly disrupt your business.
Let the Truvantis vCISO Service Manage Your Comprehensive Security & Privacy Program
Many organizations trust Truvantis, including banks, financial services, state and local government, airports, retail, healthcare & health-tech organizations, public companies, startups, large nonprofits and major sports teams.
We don't believe in one-size-fits-all security. Instead, we will create a customized program tailored to your business requirements. Our mission is to help you build practical & effective cybersecurity, privacy & compliance programs that balance budget and risk.
“We’re thrilled with the vCISO services we’ve received from Truvantis. Technical and compliance expertise is always accompanied by practical advice. I’d trust our Truvantis professional to handle anything thrown at her on behalf of our company.”
- Sarah Bimber JD, MPH, General Counsel, Amino
Truvantis offers comprehensive expertise in implementing, testing, auditing, and operating information security, privacy & compliance programs. We've helped organizations of all sizes improve their cybersecurity posture through practical, effective, and actionable programs—balancing security, technology, business impact and organizational risk appetite.
If you'd like to talk to an expert, we're here to help.
For more information on risk assessments, please download our free white paper, 6 Steps to Get Real Value out of Your Risk Assessment.
About Jerrod Montoya JD, CIPP/US
Jerrod Montoya is a business-oriented practitioner with a unique blend of legal, information security and privacy experience who aids organizations with the implementation of intelligent solutions to meet business objectives.
As a member of your Truvantis project team, Jerrod will help take your information security program to the next level. Working with Jerrod, you will learn firsthand how great it is to have someone trained and experienced in both law and security on your side.


.png)






.png)
