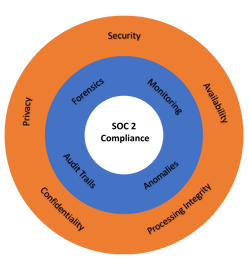
The Type 2 audit measures your organizations’ ability to maintain security, availability, processing integrity, privacy, and confidentiality operationally over time. A SOC 2 Type 2 investment helps build resiliency into your business. It demonstrates your organizations' ability to protect sensitive data in the face of today's evolving threat landscape.
The cost of response and recovery following a cybersecurity incident is often cited as one of the most expensive penalties. According to the IBM Cost of a Data Breach Report 2021:
- In 2021 it took an average of 287 days to detect and contain a data breach (data breach lifecycle).
- The average cost of a data breach in 2021 rose 10% from 2020 from $3.86M to $4.24M.
- The cost of a data breach lifecycle over 200 days was 35% (~$1.26M) higher than one with a lifecycle under 200 days.
- The most prominent incident cost savings in 2021 went to organizations with high levels of security automation, an 80% cost difference vs. organizations without automation. The difference in avg breach lifecycle was 239 vs. 324 days or 77 days.
This blog considers four operational elements of maintaining a SOC 2 Type 2 compliance program. These four high-level activities that when done right, significantly lower costs of security and increase business resiliency. These are also the areas where security automation is effective.
Monitoring for Abnormal Behavior
Once the latest vulnerability or ransomware has been well-publicized, it becomes easier to detect. A SOC 2 Type 2 program includes proactive monitoring with processes and techniques to detect abnormal network behavior that may signal unknown attacks.
Monitoring for abnormalities begins with baselining normal activity. Once normal is defined, you can monitor unusual system activity, authorized and unauthorized system configuration changes, user access levels, or unintended data flows.
Mature organizations in 2022 will use some form of a Security Event Incident and Incident Management System (SEIM) to coordinate and analyze data from various sources in the network. Data fed into the SEIM could include firewall notifications, intrusion detection system (IDS) or intrusion prevention system (IPS) alerts, vulnerability assessment reports, and operating system event logs.
Periodic independent security audits are another form of effective monitoring. For example, conducting a SOC 2 Type 2 audit and reporting exercise.
Anomaly Alerts
SOC 2 Type 2 requires the system to demonstrate the ability to send, receive and process alerts in a timely manner. SOC 2 requires alerts for any activities that lead to:
- Unauthorized exposure of data
- Changes in system control configuration
- Data transfer activities
- Privileged account access
Without AI and automation, fine-tuning alerts can be challenging. Often too many false positives lead to data analyst burnout, and signals start to be ignored. The process needs to include periodic threshold tuning to filter our false positives. Less noise enables a faster response when there is a genuine threat.
For more mature cybersecurity programs, AI and automation tools have significantly decreased the breach lifecycle.
Audit Trails
There is nothing more important than understanding the root cause of an attack. The root cause is essential to know how to respond and who is responsible. Once a breach has been detected, audit trails are critical for security operations to respond effectively. Quality audit trails generate the contextual data necessary to determine the who, what, when, where, and how the attack was executed. It is also useful when analyzing the attack based on the MITRE ATT&CK Framework and determining a cyber adversarys' Tactics, Techniques, and Procedures (TTPs). The detailed audit report should provide the breadth of the attack and its point of origin.
Actionable Forensics
It all comes down to reducing the breach lifecycle by driving down Mean-Time-To-Detect (MTTD) and Mean-Time-To-Remediate (MTTR). With actionable data in hand, you can quickly make informed decisions, mitigate the impact and implement corrective measures. With actionable forensics, you have visibility into:
- Where the attack originated
- Where it traveled in the network and what system components it impacted
- The nature of the impact (e.g., Ransomware, DDoS, Data Exfiltration)
- What to expect next
The SOC 2 Compliance Process
SOC 2 is more than ticking off the compliance checkboxes. It is a powerful business investment to lower exposure to data breaches, build trust and attract new clientele.
Maintaining SOC 2 compliance lowers costs related to cyber-incidents and helps attract new customers.
Truvantis provides full-service support for getting to your SOC 2 report. We will advise on the best approach and choices, work with you and your auditor to agree on the design of your program, and support the implementation.
Our five-step SOC 2 compliance process includes a workshop, gap analysis, implementation, mock audit, and final CPA audit report. At Truvantis, our SOC 2 service is not a one-size-fits-all solution. We take a personalized approach to your unique business situation and cybersecurity requirements.
Whether you are just beginning your journey to SOC 2 compliance or a mature organization evolving to the next level, contact Truvantis today for a consultation.


.png)





.png)
