What's new with State Privacy Laws?
There are now ten comprehensive privacy laws enacted in the United States. The new 2023 laws include those in Montana, Indiana, Iowa, Tennessee, and Texas. These laws join existing laws, including California, Utah, Colorado, Virginia, and Connecticut. These laws all share commonalities that resemble the EU's Global Data Protection Regulation (GDPR). However, the recently passed law in Tennessee stands out from all other laws in one significant way.
What is Unique about Tennessee? 
The Tennessee law enacted on May 24, 2023 codifies an affirmative defense for companies that implement and maintain alignment with the new developments of the National Institute of Standards and Technology (NIST) Privacy Framework. Specifically, Section 47-18-3213 (Privacy Program) provides that a company controlling or processing in-scope information must establish a privacy program that "reasonably conforms" to the NIST Privacy Framework and its subsequent revisions. This novel addition to comprehensive state legislation includes a variety of factors to consider in establishing such a program, including size and complexity of the organization, nature and scope of activities, sensitivity of information being processed, cost and availability of tools, and compliance with comparable state or federal law. Also under this law, a failure to maintain a privacy program in accordance with Section 47-18-3213 is considered an "unfair and deceptive act." An organization subject to a claim for violating the privacy law can mount an affirmative defense if it "creates, maintains, and complies with a written privacy program as described in Section 47-18-3213."
What is the NIST Privacy Framework?
Released in January 2020, the voluntary NIST Privacy Framework is designed to help organizations effectively address privacy considerations in their operations. 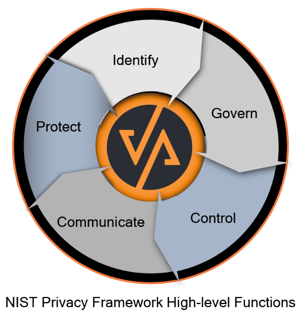 The relationship between the NIST Privacy Framework and the NIST Cybersecurity Framework is complementary. While the NIST Cybersecurity Framework primarily focuses on protecting systems and data from cybersecurity risks, the NIST Privacy Framework addresses privacy risks associated with the collection, storage, use, and sharing of personal information. The two frameworks can be used together to develop a comprehensive approach to managing an organization's privacy and cybersecurity risks.
The relationship between the NIST Privacy Framework and the NIST Cybersecurity Framework is complementary. While the NIST Cybersecurity Framework primarily focuses on protecting systems and data from cybersecurity risks, the NIST Privacy Framework addresses privacy risks associated with the collection, storage, use, and sharing of personal information. The two frameworks can be used together to develop a comprehensive approach to managing an organization's privacy and cybersecurity risks.
Why should you care?
An affirmative defense is a legal term of art, meaning that a company may be found not liable even if the party bringing the lawsuit proves their case. For example, say your organization is sued for violating the Tennessee privacy law. Your company may not be liable if it can prove that your company "reasonably conforms" to the NIST Privacy Framework as specified in Section 47-18-3213. This unique provision in the Tennessee law will surely gain attention and will most likely begin positioning the implementation of the NIST Privacy Framework as a baseline best practice.
With the NIST Privacy Framework poised for more exposure, it is worth considering some limitations and risks associated with attempting to build a program strictly based on the NIST Privacy Framework.
One limitation is that the NIST Privacy Framework is high-level and lacks specific guidance. In addition, the NIST Privacy Framework lacks key elements of recently enacted laws, which may lead to gaps without further analysis of the relationship between the Privacy Framework and applicable legislation. What it means to "reasonably conform" to the NIST Privacy Framework is not easily defined and may require the assistance of counsel or a consultant with a firm understanding of data protection. There's significant overlap with the NIST Cybersecurity Framework not fully considered in the Privacy Framework.
Three Tips for Approaching the NIST Privacy Framework
If your company is moving to "reasonably conform" to the NIST Privacy Framework, here are three tips to consider.
- Look at the Privacy and Cyber security frameworks together when building your implementation plan.
The Protect-P function has a sub-function for "Data Security," which is not very helpful. This is one example area where the Protect function in the Cybersecurity Framework can supplement and provide insights into what should be included for data security.
- Make sure you understand applicable legal requirements and map to the relevant Privacy and Cybersecurity Framework functions.
In January 2020, the GDPR was still learning to walk, and the California Consumer Privacy Act (CCPA) wouldn't be passed for another eight months. Since then, nine more laws have emerged that transition the US from a voluntary framework model into a legally mandated one. Those laws and applicable requirements must be incorporated into the voluntary framework.
- Tailor the Frameworks to your business.
The Frameworks are voluntary and designed to be tailored to your business process. NIST recognizes this and provides a caveat in the Privacy Framework, but readers tend to skip to the table and adopt the listed functions and controls at face value. Read both frameworks and customize accordingly.
![]() Jerrod Montoya, JD, CIPP/US, ISO 27001 Lead Implementer, leads the data protection team at Truvantis, Inc., a cybersecurity and data protection company. Jerrod helps companies navigate the complex world of data protection and implement reasonable security practices.
Jerrod Montoya, JD, CIPP/US, ISO 27001 Lead Implementer, leads the data protection team at Truvantis, Inc., a cybersecurity and data protection company. Jerrod helps companies navigate the complex world of data protection and implement reasonable security practices.
About Truvantis
Not every business can internally support the staffing and resources necessary for developing robust incident response programs on its own. Fortunately, you can partially or fully outsource the job of building in, training the team and running the tabletop exercises to trusted partners. At Truvantis, our vCISO service is not a one-size-fits-all solution. We take a personalized approach to your business situation, cybersecurity, privacy and incident response requirements.
Truvantis is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations and products. We specialize in helping our clients improve their cybersecurity posture by implementing testing, auditing and operating information security programs.


.png)





.png)
