Congratulations, product development was successful, and you have the utmost confidence in the capabilities of your new product or service. Engineering has assured you that the necessary controls are in place for secure operation. Sales demos are going well in the field, and your first large Healthcare or FinTech customer is ready to buy. But before the sale can proceed and contracts get signed, the client needs to review your SOC 2 report. If you planned for SOC 2 at the design phase and integrated it with the product development process and maybe have a current SOC 2 report on hand, it's smooth sailing. However, if you did not plan and initiate a SOC 2 program, you've placed your organization in peril of delaying sales and creating rework tasks for the product or service.
|
As a verb, peril is to cause to be in danger; to imperil. As a noun, peril is a situation of serious and immediate danger. A pitfall is a potential problem, hazard, or danger that is easily encountered but not immediately obvious. |
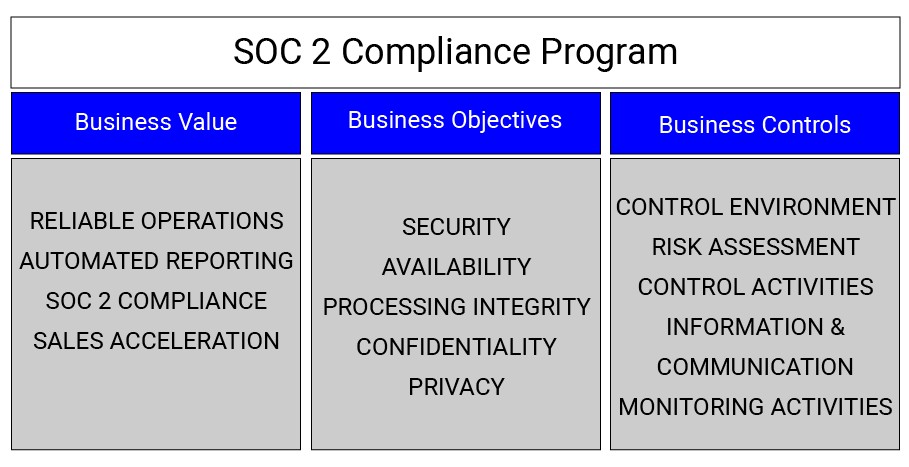
A System and Organization Controls 2 (SOC 2) compliant report is an industry-recognized standard for demonstrating the efficacy of information systems. A SOC 2 Type II report is one of the most requested credentials by prospective clients when screening IT services providers.
Achieving SOC 2 compliance is a competitive advantage, and it is often critical to making a sale. SOC 2 reports are often used throughout the industry to screen vendors early in the vendor evaluation process.
SOC 2 compliance builds trust with your clients through assurance that with the tested controls in place, your services can meet service-level agreements while maintaining information confidentiality, availability and integrity. Without a SOC 2 report, service providers can miss out on business opportunities regardless of their technology's otherwise extraordinary capabilities.
Ok, now that you're convinced that a SOC 2 Type II report is valuable to your business and possibly critical to move forward, here's some more bad news. It's an arduous, expensive, resource-intensive process and requires an outside auditor. Not only that, there are many pitfalls you may run into along the way. Here are a few potential pitfalls you might encounter and some tips for how to avoid them.
Common Pitfalls of a SOC 2 Engagement and Tips for Avoiding Them
Underestimating Time, Cost and Resources
If starting from scratch, it can take up to two years to complete a SOC 2 Type II audit. It can also be expensive in direct and opportunity costs, especially if your valuable engineering resources must be diverted from developing spectacular new product features.
Accurately determining the timeframe and quoting SOC 2 audit costs without additional context or information is impossible. There's no single SOC 2 audit size that precisely fits all. The time and money involved in a SOC 2 report depend on the scope of the exam and your current level of cybersecurity maturity.
Planning for SOC 2 Type II at the design stage and maintaining it throughout the product lifecycle will always be the most efficient method. However, if by chance you and your teams did not plan ahead, hope is not lost. You can start with a SOC 2 Type I audit which takes less time, may be accepted by your clients in the short term and can be used as a stepping stone toward achieving the full SOC 2 Type II.
For more information on the difference between SOC 2 Type I and Type II audits, please read our blog, How Much Does it Cost to Get a SOC 2 Report?
Security by Design not Implemented
Teams embroiled in product development and proof-of-concept demos often push out cybersecurity and data privacy requirements until the last minute. It's a simple fact that addressing problems early in the product life cycle (shift left) is much less expensive than doing it late in the implementation cycle (fire drill).
Sorry, there's no quick-n-easy cure for this one. However, whether or not you are building SOC 2 compliance early in the product lifecycle or in crunch mode, an expert SOC 2 consultant like Truvantis can help you create your SOC 2 report as fast and cost-efficiently as possible beginning with a gap assessment and readiness report.
The Tick Box Auditor
Unfortunately, ineffective auditing is probably the worst and most common pitfall many organizations fall into. An auditor that does not take the time to understand your business and provide you with meaningful investigations and reports beyond a simple checkbox can be worse than wasting your time. Occasionally an auditor might come in mainly looking for a way to fail the audit to either prove a point or to upsell you on a "rescue plan."
The best way to a successful audit is to be ready in advance. By the time you arrive at your audit exercise, you should be confident in passing. One way to accomplish this is to work with your expert on a gap analysis and readiness plan. An expert consultant can also help you prepare a screening process and help guide your chosen auditor to prevent the audit from getting side-tracked.
Get Started on SOC 2 Compliance Now with Truvantis
Landing customers is hard enough, don't let SOC 2 compliance become a roadblock. Having a SOC report in hand can be invaluable in pushing that deal over the finish line. So, don't wait to be asked—start now!
The task can seem overwhelming when preparing for a SOC 2 audit. One of the fastest, most cost-efficient ways to achieve SOC 2 compliance is to entrust professionals to guide you through the process. A trusted cybersecurity firm like Truvantis can help take the mystery out of the SOC 2 process. For more, please look at the Five-Step Truvantis SOC 2 Compliance Program. https://www.truvantis.com/soc-2-certification
Truvantis provides full-service support for getting to your SOC 2 report. Whether or not you are building SOC 2 compliance early in the product lifecycle or in crunch mode, we can help. We will advise on the best approach and choices, work with you and your auditor to agree on the design of your program and manage the implementation. We will then train your staff and guide you through the audit. Let's get started. Contact Truvantis today.


.png)





.png)
