Privacy regulations boil down to protecting information. In other words, privacy is about the security of data.
In today’s data-driven economy, your organization’s data is often its most valuable asset. You may be subject to multiple jurisdictions (e.g., GDPR, CCPA, HIPAA, GLBA) requiring a central privacy program capable of supporting the entire matrix of international, federal, and rapidly changing state laws and regulations.
The various privacy rights can be traced back to core security principles defined by NIST as Confidentiality, Integrity, and Availability (CIA). The various privacy regulations, regardless of approach, reach the same end: to protect the CIA of sensitive information. When organizations establish a firm foundation in security, they can implement controls that can anticipate future regulations and evolve accordingly. Privacy and security go hand in hand. Whether you take a custom approach or use an existing framework, the most effective privacy program is the one you’re going to use.
Creating an Adaptable Privacy Program
- Identify the Assets: Privacy assets are generally codified as SSN, Credit Card, or Health Information and are classified under the statute as PI, PII, PHI, etc.
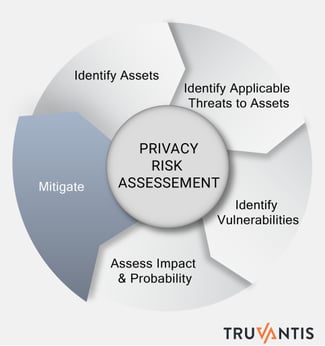 Identify Applicable Threats to the Assets: Threats can be not only people but also events or circumstances.
Identify Applicable Threats to the Assets: Threats can be not only people but also events or circumstances. - Identify Vulnerabilities: These are weaknesses surrounding or relating directly to the particular asset that, if exploited, could undermine the CIA of the asset in some way. This includes business processes.
- Assess the Impact and Likelihood: For each asset where a weakness has been identified, consider the potential impact of each threat—typically called “Threat Events.”
- Mitigate: According to ‘Reasonable Security’ best practice, organizations are required to implement controls to protect consumers’ private data.
Learn More about The intersection of Privacy and Security:
Join us at the Cybersecurity Summit Minneapolis, to hear expert advice from our Principal Security Consultant, Jerrod Montoya JD, on how you can develop and maintain a risk-based program designed to evolve with changing regulatory, threat landscape and business requirements.
In this presentation, you will hear about upcoming legal changes in privacy with an emphasis on US privacy laws, how these laws converge with best security practices, and how you can use security practices to make privacy programs more resilient to frequent changes in the law. Whether you are responsible for privacy or just a resource to a privacy group in your organization, this presentation will leave you with actionable steps to get your program on the right track.
Speaker: Jerrod Montoya JD –Principal Security Consultant, Truvantis

Jerrod Montoya is a business-oriented practitioner with a unique blend of legal, information security and privacy experience who aids organizations with the implementation of smart solutions to meet business objectives.


.png)





.png)
