William gets to the point of what a pen test should do for your business and how to avoid costly mistakes.
A penetration test is a service to the client – not an ego trip
Some pen testers try to validate themselves by trying to ‘break-in’ and thus proving that they are smarter than the defenders. So, let’s be clear – this is not a competition. Our job is to provide our clients with information and support improvement. In combination we will be stronger.
We all know who the enemies are – we must work together to defeat them. Never underestimate the creativity of a desperate adversary.
“It's fun to watch him (William) take apart a network and decide where those vulnerabilities are and then what I can do on the front end to help them.” – Rick Folkerts, Principal Security Analyst, Truvantis
We believe a penetration test simulates real world adversaries, using the same Tactics, Techniques, and Procedures (TTPs) as them. The results inform your risk assessment process which results in
- Remediation
- Preventative Control Improvements
To defend against real attackers, look at your attack surface through their lens. Have your pen tester research you through OSINT in the Surface, Deep & Dark webs to see what attackers can see.
Vulnerability Assessments, Penetration Tests and Red Teaming are Distinctly Different Tests

“Pen Testing Features the Use of Human Cunning” – Andy Cottrell, CEO Truvantis
Seven Ways to (Not) Waste Money on Pen Testing
Seven common mistakes we see in the field and what you should do about it.
Mistake One: Compliance ‘only’ Driven Scoping
What You Should Do – Research, Test and Discover Your True Attack Surface.
Scope should not be used as a defensive mechanism; it is an enhancing mechanism, used to inform the risk assessment.
Mistake Two: Only Testing ‘Exposed’ or ‘High-Risk’ Areas
What You Should Do – Test the Easiest Route and Every Foothold From There.
Mistake Three: Using Only Internal Controls to Define Attack Surface
What You Should Do - Research, Test and Discover Stuff You Didn’t Know About Including Shadow IT.
Mistake Four: Pen Testing Before Standing up a Vulnerability and Patch Management Program
What You Should Do – Stand up Your Vulnerability Patch Management Program Before Pen Testing.
Mistake Five: A Pen Test Driven Security Program
What You Should Do - A pen test is an exercise in depth, not breadth. Take a broad view and consider all of your weaknesses.
Mistake Six: Remediating Findings Without Remediating Root-cause
What You Should Do – Address the Root Cause or the Symptom Will Come Back.
Mistake Seven: Performing Pen Tests That Only Output Findings
What You Should Do – Create an Action Plan to Inform the Risk Assessment and Address Vulnerabilities. Then, Execute the Plan.
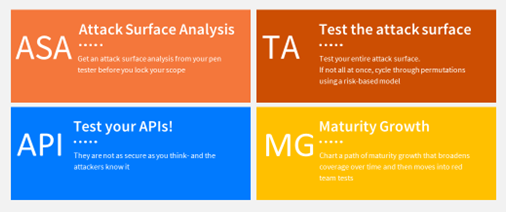
Call To Action – Test, Analyze, Grow (TAG)
William Harvy Suthers III
CISSP, OSCP, OSWP, CPT, CEH
William Suthers is the Director of Technical Services at Truvantis and an open-source security tool developer, security researcher, and security conference speaker, including HushCon and DEF CON. 
William has over fifteen years of security assessment and consulting experience with various industries, including security, SCADA, healthcare, government, military, small and large businesses, fiduciary and non-profit. He is certified by numerous security bodies, including Offensive Security, International Information System Security Consortium (ISC)², the Information Assurance Certification Review Board, and the EC-Council. His certifications include CISSP, OSCP, OSWP, CPT, and CEH.
About Truvantis
Truvantis is a security, privacy and compliance consulting firm providing best-in-class services to secure your organization's infrastructure, data, operations and products. 
At Truvantis, we've built security and privacy programs for organizations, large and small. We specialize in helping our clients improve their business resiliency and manage their business risk by implementing testing, auditing and operating information security programs.
Our world-class services include security testing and a wide range of flexible compliance and vCISO programs.


.png)






.png)
