When it comes to cybersecurity, privacy & compliance, the road forward is often unclear.
A proper risk assessment is a fundamental start to moving forward with improving your information security posture. Here are some considerations to help you get the most value from your security & privacy risk assessment.
A risk assessment is a process of identifying, analyzing, and evaluating potential risks to an organization, project, or product. It allows an organization to determine the likelihood of potential risks and their impact. It also helps organizations develop strategies to mitigate or avoid those risks.
Benefits of a Security Risk Assessment
- Guide your security investment. Use a risk assessment as a business decision-making tool. The assessment will help you to prioritize critical & urgent matters as well as determine which risks you're knowingly willing to accept.
- Risk assessments give you leverage to improve your security. It's difficult (sometimes impossible) to make dozens of changes to your cybersecurity at once. The evaluation helps prioritize tasks and make an informed investment to protect your organization.
- Risk assessments help to protect you against security breaches. Perhaps most important, companies choose to assess their risk is to protect them against costly and disruptive breaches. The risk treatments you implement after performing a risk assessment better protect your business from cyberattacks and improve protection of private data.
The Risk Assessment Stakeholders
Who is involved in the risk assessment? You'll need to organize an assessment team. Designate who will fill critical roles such as risk manager, assessment team leader, risk assessors, and any subject matter experts.
CEO Note
Top-level buy-in and support are necessary for your risk assessment and security program to be successful. A proper risk assessment will demonstrate the return on investment (ROI) the company will get on its IT security investments in comprehensive business terms.
What is the Scope of Your Risk Assessment?
It's essential to clearly define the project scope to determine the time and resources you'll need. Equally important, you'll also know what is out-of-scope. Be specific about what you're assessing. Are you assessing a product? An organizational process? A network or data center?
Opening a conversation about flaws and risks in your processes and tools can open the door to company-wide problem-solving. You can define the scope internally or in partnership with an expert, objective opinion on best defining a realistic scope.
What laws, regulations, and internal policies must you comply with?
Determine the laws, regulations, codes, standards, and internal policies to consider when assessing your risk.
Your Asset Inventory
What do you have, and what do you need to protect? After listing all your assets, you can focus on the assets you want to include in your risk assessment.
- Physical assets
- Network Hardware
- Computers
- Mobile Devices,
- Servers, etc.
- Software
- Operating Systems
- Applications
- Automation Tools
- Personnel
- Users
- Sensitive and Protected Data
- Intellectual Property
Assess Threats and Vulnerabilities
Look for any way your assets could be compromised. Outline any vulnerabilities and potential threats to the security of each. Every vulnerable asset is matched with its potential threat to form a "risk scenario." For instance, a flaw in your website's code is your vulnerability, and the threat is an attacker aiming to exploit said vulnerability.
When thinking about threats to data security, hackers are usually top of mind, but threats to your business's information security come in many different forms. For example, according to the 2022 Verizon Data Breach Report (DBR), leaving portable devices in personal vehicles is a recurring theme in data compromise statistics.
How do Attackers Find Vulnerabilities?
Many attackers are looking for easy targets with large numbers of CVEs to exploit as an opportunistic attack sales funnel.
According to the Verizon DBR, they start with scanning for IPs and open ports. Then they move to crawling for specific services. They then move on to testing for specific Common Vulnerabilities and Exposures (CVE). Finally, they try Remote Code Execution (RCE) to gain access to the system.
The average (median) organizations sampled in 2022 "run a pretty tight ship" security-wise and have relatively few CVEs per host.
Forecast Consequences & Likelihood (Risk Matrix)
Two key questions:
- Consequences: How bad would the most severe damage be if an event were to occur?
- Likelihood: What is the probability that a damaging event will occur?
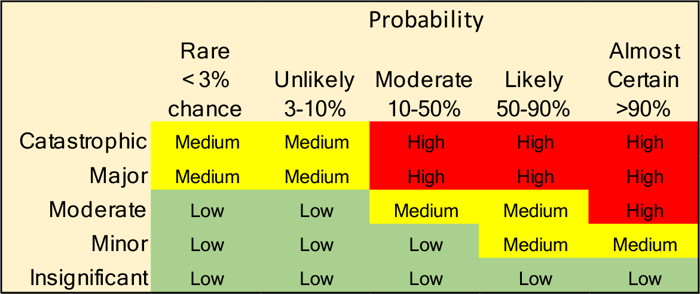
(5x5 Risk Matrix Example)
Outline a Treatment Program
All information is placed into a "risk register," which lists each risk by category and rank. The risk register has an associated "treatment plan" detailing how to potentially address each risk—for example, to accept, avoid, transfer or remediate.
The risk register and treatment plan rank each threat and vulnerability pair called a risk scenario by its severity, budget requirements, expertise needed (such as internal vs. external consultation), etc., to help you prioritize how and when to address each issue.
If You do Only one Thing to Improve Security, Please Deploy Strong Authentication
According to the 2022 Verizon DBR, over 80% of breaches can be attributed to stolen credentials. There's been an almost 30% increase in stolen credentials since 2017, cementing it as one of the most tried-and-true methods to gain access to an organization for the past four years.
"We have continued to see poor password practices as one of the leading causes of data breaches dating back to 2009. It is particularly disconcerting that so many large breaches stem from the use of default and/or shared credentials, given the relative ease with which these attacks could be prevented." (2009 DBIR page 17)."
"Those who cannot remember the past are condemned to repeat it." – George Santayana
Choose a Risk Assessment Specialist 
Truvantis® is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations, and products.
We specialize in helping our clients improve their cybersecurity posture by implementing, testing, auditing, and operating information security programs.
If you'd like to talk to an expert, we're here to help.
For more information on risk assessments, please download our free white paper,
6 Steps to Get Real Value out of Your Risk Assessment.


.png)






.png)
