Responsibility vs. Accountability for Oversight of Cybersecurity
The need to manage cybersecurity and privacy risk is generally accepted. In many organizations, it may even be clear who is doing it. However, there is often a lack of clarity over the lines of responsibility and accountability as they roll up to the board.
Let's start with one statement that is clearly true – in a corporation, the board is ultimately accountable to the shareholders for managing risk, including cybersecurity and privacy risk. In other organizations, there is always some equivalent ultimate layer of accountability.
That does not mean that the board will be doing the actual work. Other people inside or outside of the organization will be responsible for that. However, the board remains accountable.
Responsibility vs. Accountability
In casual conversation, we often use the words responsibility and accountability interchangeably. However, the difference is a hot topic in project management. For many years, RACI charts that assign names as responsible, Accountable, Consulted, and Informed for each task in a project were super popular.
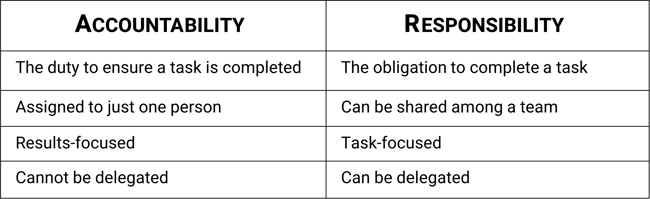
Responsibility relates to completing a task, whereas accountability relates to the oversight and subsequent examination of its success, processes, and other consequences.
While all employees of the organization are responsible for cybersecurity, you've probably seen examples of the 'accountable' CEO resigning after the information system gets hacked.
More recent thinking argues that this distinction between responsibility and accountability emphasizes the value of a senior individual over that of the team and that accountability is often more about assigning blame for failure when the planning should be more focused on avoiding that failure.
I think a more useful approach for managing cybersecurity and privacy risk, instead of looking down from the position of accountability at the people and tasks they oversee and instead look at the flow of information upwards from the accountable person.
The board defines the goals for effective cybersecurity and privacy governance program through policy and oversight. They must then charge someone with being accountable for the definition, execution, and reporting of that program.
Enter the CISO.
The CISO Role
According to standard industry jokes, CEOs keep CISOs around to have someone to fire in case of a security breach. It used to be that a cyberattack was a CISO's worst nightmare and a sure-fire sign that a pink slip would follow.
By 2020, it has become accepted that every company has been attacked (or will be). Law enforcement and cybersecurity experts have come to understand it's not the CISO's 'fault.' Ousting one will only open another can of worms, recruiting a replacement in a highly competitive market. Senior executives increasingly understand the need for the CISO role due to the business impact of security breaches on the organization.
It is impossible to reach a state of zero risk. There is always a way that something could go wrong. Organizations need to manage risk down to an acceptable level.
The CISO's role is to work with leadership to determine acceptable levels of risk for the organization. They are then accountable to the board for establishing and maintaining a corporate-wide information security management program to protect information assets.
That means that from time to time, bad things will happen that adversely affect the organization. That is what a non-zero risk means. You can keep firing the CISO every time if you like, but the cost of replacement is high. According to Cybersecurity Ventures, in 2016, annual CISO compensation in the largest U.S. cities was topping out at between $380,000 and $420,000 and expects to see an increase in organizations moving the needle to the $500,000 to $1 million range over the next five years.

A virtual CISO (vCISO) service can help bridge the gap when a company is between CISOs or a permanent solution. Truvantis offers world-class vCISO services customized to the scope and objectives of your organization.
There are several reasons why the CISO roles and responsibilities are becoming a critical issue within enterprises. The increasing risk of data and system compromise, regulatory compliance, the multinational aspects of information traveling across borders, emerging technology, and the demand for external auditor reports have elevated the CISO position to be a hot topic of discussion among the board and senior executives.
The CISO role evolves from a strict technology focus to a process and business focus.
Traditionally, the CISO position evolved from the IT environment where IT technologists, by default, were responsible for the fundamentals of IT security of the information system. Generally, IT technologists lack interest in the entire business transitions of the organization.
Things are changing; transforming the CISO role from the technical to the business side is based on the rapid change of business rules dictated by various and complex regulatory compliance requirements. Classic examples are the EU General Directive Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), where emerging modern laws increase legal liability risk.
To whom should the CISO report? Information security governance is the responsibility of the board of directors and senior executives. The ISO/IEC 27001standard states that top management shall demonstrate and ensure that the information security policy and the information security objectives are established and compatible with the organization's strategic direction and the integration of information security requirements into the organization's processes.
If an organization agrees with this statement, the CISO position should be elevated and reported to the CEO or, even better, General Counsel to ensure independent operation. On the other hand, suppose the organization confines cybersecurity within the IT function. In that case, conflicts between operation progress and meeting risk management objectives are resolved at the CIO level, rather than the executive team or board where such decisions belong.
Do organizations fully understand cybersecurity functions?
CISOs face the challenge of justifying the approval of the cybersecurity budget, which can be challenging to explain within an organization. The cybersecurity portfolio solution requires a much shorter span of periodic evaluation than the general IT portfolio solution. Security is dynamic, with some reactionary mode, and it changes based on new threats, incidents, and new regulations.
The Board Must Own the Policies
Another reason CISOs need to bridge the gap from technology to the business domain is that security and privacy policies need to be understood by the board, who are accountable for ensuring that they are appropriate. The technology side provides the underlying details on how technology will assist in implementing the security policy passed down from the board or its executive management.
We often see a reverse process where the IT team decides they need a policy, which they create and send to the board or executive management for approval. Sometimes the board or CEO signs off without fully understanding the technical details or the associated business issues.
In summary
So the board is accountable to the shareholders, and the CISO should be accountable to the board. The CISOs team may hold other staff accountable for parts of the security and privacy program. But responsibility for individual tasks lies everywhere – indeed, all employees of the organization are responsible for cybersecurity in some way.
Most importantly, the board owns it, knows they own it and plans to manage the risk to meet shareholder expectations.
Take Action
There's always a way forward to improve cyber-governance, risk mitigation, and corporate resilience. Your business situation and cybersecurity requirements are unique. Tell us about them.
At Truvantis, our vCISO service is not a one-size-fits-all solution. We take a personalized approach to your unique business situation and cybersecurity requirements.
Truvantis® is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations, and products. We specialize in helping our customers improve their cybersecurity posture by implementing, testing, auditing, and operating information security programs.


.png)





.png)
