Ok, so you had a data breach. What do you do next?
Some experts warn that it's not a matter of 'if' but 'when' your information management system will get breached. Time-to-detection and time-to-recovery are essential factors of business continuity. What steps should you take in case of a data breach, and whom should you contact?
|
According to the IBM Cost of a Data Breach Report 2022:
|
Proactive & Reactive Security
Securing organizations against cyberattacks is a continuous process as attackers constantly seek new methods. An effective security program combines both proactive and reactive security efforts.
Proactive security helps comply with laws and regulations, protect against known attack vectors and build business continuity and disaster recovery plans for when events occur.
Reactive security deals with events after they have occurred. A mature, proactive security program helps your reactive approach become quicker and more effective when needed.
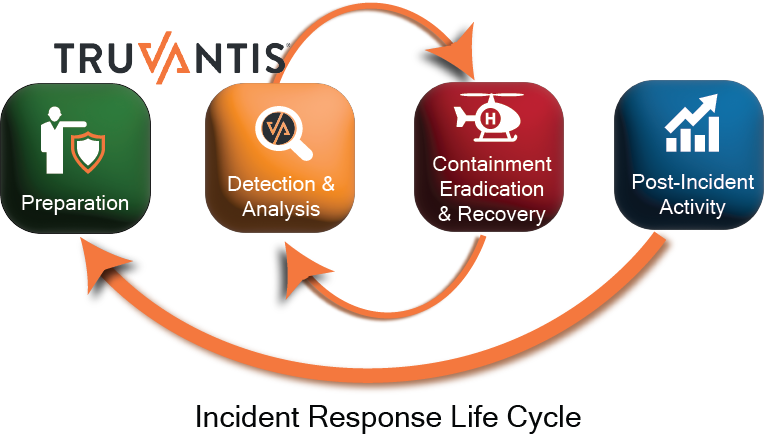
Effective incident response relies on being prepared. Maintaining a mature cybersecurity program and having a plan of attack for when incidents occur is vital to limiting the damage of ransomware and data exfiltration attempts on your organization.
RespondActivate the Breach Response Team Secure Your Operations Eradicate, Recover and Mitigate Vulnerabilities Have a communications plan Notify Appropriate Parties
|
PrepareContinuous Improvement Metrics Share Actionable Information Have a Plan for Recovery Cybersecurity Training Rehearse – tabletop exercises
|
To learn more about strengthening the effectiveness of your breach response, please click here.
About Truvantis
Not every business can internally support the staffing and resources necessary for developing robust incident response programs on its own. Fortunately, you can partially or fully outsource the job of building in, training the team and running the tabletop exercises to trusted partners. At Truvantis, our vCISO service is not a one-size-fits-all solution. We take a personalized approach to your business situation, cybersecurity, privacy and incident response requirements.
Truvantis® is a cybersecurity consulting organization providing best-in-class cybersecurity services to secure your organization's infrastructure, data, operations and products. We specialize in helping our clients improve their cybersecurity posture by implementing testing, auditing and operating information security programs.


.png)





.png)
