Many Organizations are Finding Value in Continuous Compliance
In 2023, many organizations are considering cybersecurity and privacy as business accelerators. That means compliance with security and privacy regulations and programs is more prominent in the organization and drives a move to adopt continuous compliance.
In the past, compliance has been perceived as a necessity, a box to check, and often a burden. The cost of manual compliance and the time it takes away from other vital priorities caused many leaders to treat compliance as a necessary evil. However, in the past few years, compliance has seen great strides that enable scalability, reduced manual effort, and a better alignment with security and privacy concepts.
This shift is directed by the maturing of risk management approaches. Companies are moving away from reactive and manual methods into a proactive posture driven by automation. Many organizations now treat compliance as a means to mature security, privacy and risk reduction practices.
In turn, compliance becomes a business accelerator leading to greater organizational trust, shorter sales cycles, gains in competitive differentiations, and greater visibility into their compliance posture.
Continuous compliance is a proactive approach to maintaining frameworks and regulatory requirements on an ongoing basis. As a proactive approach, the goal is to continuously maintain requirements as part of daily operations, not just during an audit.
A Brief History of Risk and Compliance
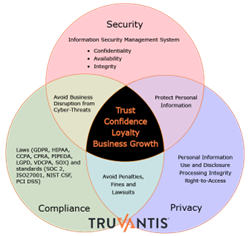
While HIPAA and its security and privacy requirements were released in 1996, it took almost a decade to gain traction in the healthcare industry. In 2010, the AICPA released SSAE 16, which birthed the SOC 2 audit framework and its take on security and privacy requirements, amongst other categories. Separately, in 2005, the International Organization for Standardization's (ISO) initial release of ISO 27001 for security and later ISO 27701 focused on privacy. In 2018, the EU released GDPR, and California passed the CCPA to protect the data of its citizens.
During this time, compliance was frequently treated as a checkbox that organizations must align with to prevent fines and reduce the possibility of security and privacy incidents. Organizations of all sizes see compliance as a burden, periodically forcing them to redirect resources to the compliance audit/assessment of the day versus focusing on the business. And it gets even worse with programs such as SOC 2 Type II, where the evidence required to present needs to cover six to 12 months.
This is the problem with all point-in-time audits/assessments. They cause the organization to only focus on complying with the program at that point-in-time and not complying with it all the time. While point-in-time compliance offers the foundation for security and privacy, it is missing the critical element that allows an organization's security and privacy programs to evolve from reactive to proactive.
The Rise of Continuous Compliance
Organizations require constant vigilance to achieve proactive compliance as technology usage becomes more critical to the organization's success. To accomplish this, organizations are moving to continuous compliance across people, processes, and technology, resulting in continuous visibility of the status of risk and compliance controls.
More specifically, continuous compliance bridges the gap between scheduled third-party validation (attestations and audits) and compliance in real-time. Organizations gain security and privacy capabilities otherwise unavailable in a point-in-time or manual compliance environment. Continuous compliance rapidly evolves and replaces checkbox compliance concepts with proactive security and privacy monitoring.
Shifting from point-in-time to continuous compliance
How Often do Organizations Review Compliance Controls
Compliance is as much a trust-building exercise as it is the foundation for building mature security, privacy and risk management programs. One of the leading indicators that an organization is building a mature compliance program is that it can provide evidence beyond the requirements of individual frameworks.
Point-in-time compliance meets the bare minimum requirements to protect information. With point-in-time, security, privacy and risk management can become deprioritized because of other business goals or initiatives. However, mature organizations are taking advantage of continuous compliance to gain daily or real-time visibility into the status of their security, privacy and risk management programs while reducing the resource load of achieving and maintaining compliance.
Take, for example, the AICPA's SOC 2 Type II audit report that assesses the security controls of a service organization over twelve months. During the attestation window, organizations provide necessary evidence to a CPA firm auditor to demonstrate that a company has the required controls to secure and protect sensitive information.
Adopting an automated solution enables organizations to move to a mature compliance status that allows proactive efforts. These proactive efforts build confidence and increase trust internally and externally.
Reactive Compliance
Point-in-time compliance programs force teams into a position of only prioritizing compliance with their security, privacy and risk programs at the time of the audit/assessment. Without regular testing and evidence collection, issues develop that prevent a team from understanding that security or privacy controls are not functioning correctly until, most times, well after the fact. This results in business interruptions, security breaches, fines, and a loss of customer trust in the organization.
Achieving Continuous Compliance
The journey towards continuous compliance reduces many of the risks of point-in-time compliance and can help lead to business acceleration. Processes and human resources alone cannot sufficiently fulfill the requirements necessary to achieve continuous compliance. Technology plays a critical role in scaling compliance capabilities, particularly the automation of testing and evidence collection. Ongoing compliance is performed at the intersection of people, processes, and technology—a common theme among many robust cybersecurity concepts.
Beyond saving time and resources, continuous compliance can improve an organization's security posture and help build trust.
Potential Benefits of Continuous Compliance:
- Improved security, privacy and risk management postures
- Better efficiency in security and privacy reviews
- Improved visibility to identify and manage risks
- Increased trust from leadership
- Increased protection from external threats
- Strengthened relationships with existing customers
- Increased protection from internal threats
- Ability to differentiate from competitors
- Increased focus on other key business priorities
- Easier to attract new customers
- Increased revenue
Proactive, Continuous Compliance Builds Trust and Accelerates Business
Point-in-time compliance lacks the necessary scalability or ability to incorporate the concept of trust through transparency. On the other hand, a continuous compliance program can build trust through increased visibility, save time and resources on achieving and maintaining regulatory compliance, and shift more energy to accelerating the business.
Continuous Compliance as the Foundation of Security, Privacy and Risk Management
Historically, compliance has always been a strong foundation for security, privacy and risk management programs. Achieving a proactive or active state of compliance offers clients and stakeholders visibility into an organization's security, privacy and risk postures. Automation reduces blind spots through constant verification—which is the key to building trust—but more importantly, reduces the time to identify and address out-of-compliance conditions.
Although there are many use cases for why continuous compliance is necessary to maintain a mature security, privacy and risk management posture, one of the most common concerns is the scalability of the compliance program as an organization changes and grows.
Drivers Towards Compliance Maturity
Achieving a continuous or proactive state of compliance enables organizations to build trust, accelerate the business, and even extend into security and privacy capabilities.
Teams are being asked to do more with fewer resources and staff. Organizations that achieve some level of continuous compliance put less of a burden on other organizational priorities and are better equipped to demonstrate the value of their security, privacy and risk management programs.
Advice from the Expert
According to Jeff Hall, Principal Security Consultant at Truvantis, the American Institute of Certified Public Accountants (AICPA) has been promoting the concept of a continuous audit since the early 1990s. The idea is that you're continually reviewing what's going on in the business in one way, shape or form. That could mean running daily automated reviews of things like change control tickets to ensure they are appropriately scrutinized and approved before closing them.
In continuous compliance, there is a lot of talk about automation. That doesn't necessarily mean you must rush out and buy expensive new tools. Do you have a toolset that you've already purchased? It likely has ways to provide methods to implement continuous compliance. For example, if you're using ServiceNow, you can do much of this within the ServiceNow world. You do not necessarily have to buy a new tool.
The first thing to know is your environment and what you are trying to accomplish. Then it would help if you examined the tools you have. And many of those tools already have APIs or even continuous compliance reporting/queries that you can use to build dashboards and reports to look for exceptions to your policies, standards and procedures.
Says Hall, " Nine times out of ten. The toolset you already have will do it for you. You just have to program it correctly. People think there's magic behind toolsets. There isn't any magic. It's just looking at what you've got and what you're trying to do. What do you want to audit and know what is important? I would say just use automation as it exists. I've always told my clients that you want to eliminate exceptions because those are the things that trip you up when you go into a PCI audit, for example."
It's essential to eliminate exceptions caused by silly mistakes versus ignoring them. For example, make sure your data sets, such as change logs and helpdesk records, have correct dates and approvals.
"For example, you don't want to have a JIRA ticket closed before it was opened. Or change tickets that get closed even though they were never signed off by management. Really at the end of the day, there's no excuse for those mistakes. They should never happen. And yet they still do well because no one is going back and making sure that all those exceptions aren't there. That's what continuous audit is all about: keeping procedural exceptions from occurring in the first place. But if they happen, recognizing them quickly and addressing them doesn't have to take a new tool."
About Truvantis
Truvantis is a cybersecurity consulting organization with comprehensive expertise in implementing, testing, auditing, and operating information security, privacy and compliance programs. We specialize in helping our clients improve their cybersecurity posture through practical, effective, and actional programs – balancing security, technology, business impact and organizational risk appetite.
About Jeff Hall CISA, CISM, CDPSE, PCI QSA
Jeff Hall is a Principal Security Consultant at Truvantis and was the founding President of the Minnesota InfraGard chapter, the public/private partnership between businesses and the US Federal Bureau of Investigation (FBI).


.png)






